Cyberwal in Galaxia
2023 Cyberwal in Galaxia Program
This school is free of charge* (registration below)
04 – 08 December 2023 (end of registrations on 27/11)
This program will take place on the Galaxia site in Transinne which, together with the European Space Agency (ESA) and the ESEC Centre in Redu (5 km away), forms a leading Space center in Europe.
Together for Cybersecurity - Investing in cybersecurity for a secure future -
Together for Cybersecurity - Investing in cybersecurity for a secure future -
It is in the ESEC Centre in Redu that ESA has decided to base its cybersecurity center, which will ensure the cyber protection of the Agency’s ground and airborne activities.

It is in the ESEC Centre in Redu that ESA has decided to base its cybersecurity center, which will ensure the cyber protection of the Agency’s ground and airborne activities.

The Euro Space Center is an educational center dedicated to Space, which welcomes 15,000 young people per year, of 35 different nationalities, for 3 to 5 days of courses, as well as 70,000 visitors per year.
The Euro Space Center is an educational center dedicated to Space, which welcomes 15,000 young people per year, of 35 different nationalities, for 3 to 5 days of courses, as well as 70,000 visitors per year.


The Euro Space Center has an auditorium of 150 seats (including 4 seats for people with reduced mobility).
Its 30:10 screen offers a great flexibility for presentations, as does its Smart Board interactive screen. The recording option definitely makes this room a cutting-edge auditorium!
Cyberwal in Galaxia
Speakers
The objective of the organizers is to position these courses as a high level of education, on a European scale, and to link them directly to the needs of the cyber ecosystem.
Cyberwal in Galaxia
Speakers
The objective of the organizers is to position these courses as a high level of education, on a European scale, and to link them directly to the needs of the cyber ecosystem.

Pascal Rogiest

Michele MOSCA

Maxime Cordy
President of the Scientific Committee
Our Program for the 5 days
The program includes theoretical & practical courses.
A break is scheduled every day in the morning and afternoon.
The next editions of Cyberwal in Galaxia Program are already planned for 2024.
- Day 1
Monday 04/12
- Day 2
Tuesday 05/12
- Day 3
Wednesday 06/12
- Day 4
Thursday 07/12
- Day 5
Friday 08/12
Sold out
AI and Cybersecurity Day
The rise of artificial intelligence (AI) is having a profound impact on our society. AI is already being used in a variety of key areas such as self-driving cars where AI is being used to develop (1) self-driving cars that can navigate roads and avoid obstacles without human intervention, (2) AI based virtual assistants such as Siri and Alexa that can answer questions, make appointments, and control smart home devices, (3) medical diagnosis where AI is being used to diagnose diseases more accurately than human doctors, (4) financial trading where AI is being used to trade financial assets more efficiently than human traders and (5) customer service where AI is being used to develop chatbots that can answer customer questions and resolve issues without human intervention. AI is driving innovation by providing improved efficiency, increased productivity, better decision-making, improved healthcare, or environmental sustainability.
However the rise of AI is also creating new cybersecurity risks that make AI systems vulnerable to new types of cyberattacks, that could have a significant impact on businesses and organizations. Cybersecurity is important for AI systems because they are becoming more complex and interconnected which makes them more vulnerable to cyberattacks, they are being used to collect and store sensitive data, they are often being used in real-time applications, and they are often used in adversarial environments where attackers are constantly trying to find ways to exploit vulnerabilities in AI systems. Cybersecurity is also important for AI because AI systems are increasingly being used in critical infrastructure, such as power grids and transportation systems. If these systems are hacked, it could have a devastating impact on society.
The objective of the day is to present some key research topics at the intersection of AI and cybersecurity in the form of short tutorials or research presentations. The day will address research topics on the use of AI for improving cybersecurity as well as improving the protection of AI systems. Key research areas at the intersection of AI and cybersecurity that will be covered include AI based identification, protection, detection, response and recovery. More specific topics such as AI based AI-powered anomaly detection, AI-powered malware detection, AI-powered incident response and AI-powered ethical hacking will also be addressed.
8:30 AM – 9:00 AM
REGISTRATIONS
9:00 AM – 9:15 AM
- Auditorium
Introduction
- AI in Cyber Security leverages the industrial cyber security power of machine learning and data analysis to augment traditional security measures.
- Zero Trust Architecture brings a new security level in OT/ICS environment.
- How can the Industrial Metaverse help to secure our Industry 4.0 ?

Philippe Massonet - Scientific Coordinator at CETIC

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

David Prada
9:15 AM – 10:45 AM
- Auditorium
The Intersection of Cybersecurity and AI: Opportunities and Challenges
In today’s digital economy, where data breaches plague industry and government alike, the fusion of Cybersecurity and Artificial Intelligence (AI) has emerged as a potent defense strategy. This talk explores the symbiotic relationship between AI and cybersecurity, delving into both its promises and perils.
AI has revolutionized cybersecurity, enabling advanced capabilities such as the detection of malware, vulnerabilities and fraud. Yet, as AI empowers defenders, it also empowers attackers. The dark side of AI reveals a landscape where malicious actors harness AI for spear phishing, automated cyberattacks, misinformation, and deepfakes. Moreover, AI itself becomes a target, as shown by adversarial machine learning and model poisoning attacks. Finally, there are concerns about AI creating a dystopia.
The talk further delves into novel technologies such as attribution (watermarking) and computing on encrypted data that can play a role in mitigating some of these risks.
Overall, there is a need for a multidisciplinary approach encompassing technology, regulation, and ethics to effectively address the challenges presented by the intricate relationship between AI, cybersecurity and privacy.

Bart Preneel - Full Professor, KU Leuven

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

David Prada
10:45 AM – 11:00 AM
COFFEE BREAK
11:00 AM – 12:15 AM
- Auditorium
Don't date the robots: the bad marriage between ML and Security
- AI in Cyber Security leverages the industrial cyber security power of machine learning and data analysis to augment traditional security measures.
- Zero Trust Architecture brings a new security level in OT/ICS environment.
- How can the Industrial Metaverse help to secure our Industry 4.0 ?

Gabriele Costa - Associated professor at IMT

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

David Prada
12:30 PM – 01:30 PM
LUNCH TIME
1:30 PM – 2:30 PM
- Auditorium
Machine Learning Security in the Real World
Adversarial attacks are considered as one of the most critical security threats for Machine Learning (ML). In order to enable the secure deployment of ML models in the real world, it is essential to properly assess their robustness to adversarial attacks and develop means to make models more robust. Traditional adversarial attacks were mostly designed for image recognition and assume that every image pixel can be modified independently to its full range of values.
In many domains, however, these attacks fail to consider that only specific perturbations could occur in practice due to the hard domain constraints that delimit the set of valid inputs. Because of this, they almost-always produce examples that are not feasible (i.e. could not exist in the real world). As a result, research has developed real-world adversarial attacks that either manipulate real objects through a series of problem-space transformations (i.e. problem-space attacks) or generate feature perturbations that satisfy predefined domain constraints (i.e. constrained feature space attacks). In this talk, we will review the scientific literature on these attacks and report on our experience in applying them to real-world cases.

Maxime Cordy - Research Scientist at the Interdisciplinary Center for Security, Reliability and Trust (SnT)

Laurens Singier - Cybersecurity IT/OT researcher , Ethical hacker

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.
2:30 PM – 3:30 PM
- Auditorium

Re-envisioning ML's role in cybersecurity - after burning down ML-NIDS
Training
- Introduction to Industrial Control Systems
- Basics of PLC Programming
- Industrial Communication
- Scanning ICS networks
- Industrial Network & System enumeration
- Reversing proprietary industrial protocols
- Exploiting industrial control systems
Workshop
Hands on: Industrial CTF on the Fictile Factory

Laurens D'hooge - PhD student at IDLab, Ghent University, in collaboration with imec

Laurens Singier - Cybersecurity IT/OT researcher , Ethical hacker

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.
3:30 PM – 3:45 PM
COFFEE BREAK
3:45 PM – 4:30 PM
- Auditorium
Secure federated learning applied to medical imaging with fully homomorphic encryption
The course aims to introduce students to the understanding of different Federated Learning concepts with a focus on security vulnerabilities and cybersecurity challenges. The course will introduce the Federated Learning and compare it to other Machine Learning approaches. The main concepts and process of Federated Learning will then be presented. The model aggregation phase will then be presented along with the security threats.
The concept of differential privacy and its relevance for federated Learning explained. Homomorphic encryption techniques will then be introduced for securing the federated Learning process. The course will then present open-source frameworks for federated learning that will be used in the practical work. The practical work aims at applying Federated Learning concepts with a practical exercise from the medical/hospital domain (classification of medical images (malignant or benign lesions)).
The practical work will cover the steps required to train a neural network (CNN) with a Federated learning architecture. The practical work will involve adapting the model to meet cybersecurity challenges and performing cybersecurity tests.
Training
- Introduction to Industrial Control Systems
- Basics of PLC Programming
- Industrial Communication
- Scanning ICS networks
- Industrial Network & System enumeration
- Reversing proprietary industrial protocols
- Exploiting industrial control systems
Workshop
Hands on: Industrial CTF on the Fictile Factory

Xavier Lessage - Senior Research Engineer in the Data Science Department at CETIC

Laurens Singier - Cybersecurity IT/OT researcher , Ethical hacker

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.
4:30 PM – 5:15 PM
- Auditorium
Using AI to enhance cybersecurity
In today’s dynamic cybersecurity landscape, the escalating cyber threats demand advanced methodologies for detection and characterization. This talk explores the pivotal role of Artificial Intelligence (AI) as a technological enabler in significantly fortifying cybersecurity measures. Two key applications of AI in this context will be discussed: leveraging AI as a robust threat detector within network environments and harnessing its capabilities to enhance the identification of cyber vulnerabilities.
The first part of the presentation delves into the application of AI techniques for the systematic detection and classification of cyber threats in network environments. This strategic characterization serves as the cornerstone for developing advanced solutions geared towards enhancing the overall cybersecurity posture of networks. Practical insights will be provided, using Operational Technology (OT) networks as a compelling use case to illustrate the effectiveness of AI-driven threat detection.
The second part of the talk explores the transformative potential of AI in automating and elevating penetration testing (pentesting) tools for the identification of system vulnerabilities. This discussion aims to highlight the proactive role of AI in fortifying systems against potential cyber threats, thereby enhancing their overall resilience in an ever-evolving digital landscape.

Eric Viseur - Ingénieur système at Thales

Laurens Singier - Cybersecurity IT/OT researcher , Ethical hacker
5:30 PM – 6:30 PM
- Parc Galaxia
The Galileo Integrated Logistics Centre, where Galileo Ground Segment Operations begin.
Galileo’s satellites communicate with 16 ground stations and these, in turn, ensure that the Galileo constellation continues to deliver reliable accurate and secure positioning and timing. To allow these stations to operate to the highest standards, they need to have easy access to highly specialized parts that can be rapidly delivered to where they are needed. The Galileo ILS Centre is the go-to point for those managing ground stations and is staffed with highly qualified engineers specialized in robotics, aeronautics and IT.
From its central location in Transinne, the Galileo ILS Centre is supporting an efficient spare part and repair provisioning service for Galileo ground infrastructure. The Centre is in charge of guaranteeing the proper spare part stock for corrective and preventive maintenance. It is also resetting and updating equipment received from the stations, or shipping it to the manufacturers for more comprehensive retrofits, should this be necessary.


Nicky Carlomagno - Head of SATNAV Services

Laurens Singier - Cybersecurity IT/OT researcher , Ethical hacker
Sold out
Quantum Day
8:30 AM – 9:00 AM
REGISTRATIONS
09:00 AM – 10:30 AM
- Auditorium
Introduction to Quantum Computing & Quantum Cryptography - Key Research Trends
This presentation provides a succinct overview of the foundational principles of quantum computing and quantum cryptography, focusing on current research trends that are shaping these fields. Attendees will gain insights into quantum algorithms, quantum hardware developments, and advancements in cryptographic techniques based on quantum principles. The discussion will highlight key challenges and opportunities in harnessing quantum phenomena for practical applications, emphasizing the interdisciplinary nature of quantum research. Join us to explore the forefront of quantum technologies and their transformative potential in revolutionizing computation and information security.

Professor Michele MOSCA - Co-founder of the Institute for Quantum Computing at the University of Waterloo, CEO & co-founder of evolutionQ

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

Benoit Balliu - Howest Researcher in Industrial Security.
10:30 AM – 11:00 AM
COFFEE BREAK
11:00 AM – 12:30 PM
- Auditorium
Quantum Keys Distribution over Satellite – Singapore Initiatives
This presentation unveils Singapore’s groundbreaking initiatives in quantum key distribution (QKD) over satellite communication channels. We delve into the cutting-edge research and development efforts aimed at establishing secure quantum communication links between ground stations and satellites. Explore the technological advancements, key milestones, and the role of Singapore in pioneering quantum-secured satellite communication. Join us to learn about the implications of these initiatives for global secure communication and data encryption in the quantum age.

Robert Bedington - Co-Founder & CTO at SpeQtral

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

Benoit Balliu - Howest Researcher in Industrial Security.
12:30 PM – 02:00 PM
LUNCH TIME
2:00 PM – 3:30 PM
- Auditorium
High-performance Quantum Technology – Continuous Variable QKD
This presentation introduces continuous variable quantum key distribution (CV-QKD) as a high-performance quantum technology. We explore the principles and applications of CV-QKD, emphasizing its potential for achieving secure and high-speed quantum communication. Through a discussion of recent advancements and practical implementations, attendees will gain insights into the promising future of CV-QKD in enabling robust and efficient quantum-secured communication networks. Join us to uncover the key developments and innovations in this field, paving the way for a more secure digital era.

Professor Xin Yin - Professor at IMEC and University of Ghent, Director of IDlab

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

Benoit Balliu - Howest Researcher in Industrial Security.
3:30 PM – 4:00 PM
COFFEE BREAK
4:00 PM – 5:00 PM
- Auditorium
International Operational Usecases of QKD to protect existing business applications
This presentation sheds light on the INT-UQKD program, showcasing how Quantum Key Distribution (QKD) is being strategically employed to safeguard existing business applications on a global scale. We delve into practical use cases, highlighting successful implementations of QKD in diverse operational environments. Through real-world examples and case studies, attendees will gain insights into the tangible benefits of integrating QKD into their existing security infrastructure. Join us to explore the transformative potential of QKD in fortifying information security for businesses worldwide.

Dr. Pascal Rogiest - Chief Commercial Officer of RHEA Group

Benoit Balliu - Howest Researcher in Industrial Security.
05:15 PM – 08:45 PM
VIP Euro Space Center visit

- Moonwalk/Marswalk XP: Set your foot on the Moon and Mars
- Multi-axis chair: Test your reactions in a disorientation situation
- Space Flight Unit: Take control of your spaceship
- Free Fall Slide: Let yourself go into free fall
- Space Rotor: Feel the centrifugal force
- Mars Village: Get ready for life on Mars
In small groups, live a unique experience combining discovery and space simulations!
You will see demonstrations of 5 training simulators and discover the planet Mars as if you were there.
Industry and challenges Day
9:00 AM – 9:30 AM
REGISTRATIONS
9:30 AM – 10:45 AM
- Auditorium
Training in Cybersecurity: challenges and next steps
The shortage of people with the right skills, particularly in cybersecurity, is now well established. According to Gartner, over the next few years, there will be a shortfall, worldwide, of 3.4 million experts in this field .
However, it’s never too late to tackle the issue.
We invite you to discuss this issue, during the 2023 Cyberwal in Galaxia school, with players who are active in the ecosystem and ready to collaborate on this topic.
The workshop will be divided into 2 parts:
1) What challenges were identified by the various players and what are their current concerns?
2) How can we work together to find and implement quick wins but also tackle the underlying issues?

Jeremy Grandclaudon - Co-leading the program Cyberwal By Digital Wallonia at ADN.

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

Benoit Balliu - Howest Researcher in Industrial Security.
10:45 AM – 11:00 AM
COFFEE BREAK
11:00 AM – 12:30 PM
- Auditorium
Training in Cybersecurity: challenges and next steps
The shortage of people with the right skills, particularly in cybersecurity, is now well established. According to Gartner, over the next few years, there will be a shortfall, worldwide, of 3.4 million experts in this field .
However, it’s never too late to tackle the issue.
We invite you to discuss this issue, during the 2023 Cyberwal in Galaxia school, with players who are active in the ecosystem and ready to collaborate on this topic.
The workshop will be divided into 2 parts:
1) What challenges were identified by the various players and what are their current concerns?
2) How can we work together to find and implement quick wins but also tackle the underlying issues?

Jeremy Grandclaudon - Co-leading the program Cyberwal By Digital Wallonia at ADN.

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

Benoit Balliu - Howest Researcher in Industrial Security.
12:30 PM – 01:45 PM
LUNCH TIME
01:45 PM – 01:50 PM
- Freedom & ISS
Introduction
A meticulously designed CTF challenge that pushes the boundaries of conventional cybersecurity knowledge. Attendees will be able to revel in the opportunity to listen to and interact with esteemed experts from the cybersecurity domain, each bringing a wealth of experience and fresh perspectives.
Complementing these, our hands-on demonstrations promise a deep dive into the latest technologies and methodologies, forging a link between academic theories and their tangible, real-world implementations. Join us for a comprehensive exploration of the future of cybersecurity.
Deloitte will invite keynote speakers to develop concise and insightful talks on a relevant cybersecurity topic and allow some time for questions and answers.
01:50 PM – 05:00 PM
- Freedom & ISS
Capture The Flag (CTF)

Arthur Testa & Loïc Sicquet - at Deloitte
You are free to move from one room to another according to your interests
01:45 PM – 01:50 PM
- Auditorium
Introduction
A meticulously designed CTF challenge that pushes the boundaries of conventional cybersecurity knowledge. Attendees will be able to revel in the opportunity to listen to and interact with esteemed experts from the cybersecurity domain, each bringing a wealth of experience and fresh perspectives.
Complementing these, our hands-on demonstrations promise a deep dive into the latest technologies and methodologies, forging a link between academic theories and their tangible, real-world implementations. Join us for a comprehensive exploration of the future of cybersecurity.
Deloitte will invite keynote speakers to develop concise and insightful talks on a relevant cybersecurity topic and allow some time for questions and answers.
01:50 PM – 02:30 PM
- Auditorium
Red Teaming vs. Blue Teaming
A meticulously designed CTF challenge that pushes the boundaries of conventional cybersecurity knowledge. Attendees will be able to revel in the opportunity to listen to and interact with esteemed experts from the cybersecurity domain, each bringing a wealth of experience and fresh perspectives.
Complementing these, our hands-on demonstrations promise a deep dive into the latest technologies and methodologies, forging a link between academic theories and their tangible, real-world implementations. Join us for a comprehensive exploration of the future of cybersecurity.
Deloitte will invite keynote speakers to develop concise and insightful talks on a relevant cybersecurity topic and allow some time for questions and answers.

Arthur Testa - at Deloitte
02:30 PM – 03:45 PM
- Auditorium
Digital Wallet
A meticulously designed CTF challenge that pushes the boundaries of conventional cybersecurity knowledge. Attendees will be able to revel in the opportunity to listen to and interact with esteemed experts from the cybersecurity domain, each bringing a wealth of experience and fresh perspectives.
Complementing these, our hands-on demonstrations promise a deep dive into the latest technologies and methodologies, forging a link between academic theories and their tangible, real-world implementations. Join us for a comprehensive exploration of the future of cybersecurity.
Deloitte will invite keynote speakers to develop concise and insightful talks on a relevant cybersecurity topic and allow some time for questions and answers.

Joran Frik - at Deloitte
03:45 PM – 04:30 PM
- Auditorium
Zero Trust

Dhiren Patra - at Deloitte
04:30 PM – 05:00 PM
- Auditorium
Cyber Awareness and Social Engineering

Nicolas Noël - Director, Cyber Risk Advisory at Deloitte

Etienne Caron - Manager, Cyber Risk Advisory at Deloitte
IoT Day
9:00 AM – 9:30 AM
REGISTRATIONS
9:30 AM – 10:30 AM
- Auditorium
The future of OT/ICS security: 3 solutions
- AI in Cyber Security leverages the industrial cyber security power of machine learning and data analysis to augment traditional security measures.
- Zero Trust Architecture brings a new security level in OT/ICS environment.
- How can the Industrial Metaverse help to secure our Industry 4.0?

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.

Tijl Atoui - Howest Cybersecurity Teacher and Researcher in Industrial Security and Fictile Factory maintaining

David Prada
10:30 AM – 11:00 AM
- Auditorium
Introduction to OT/ICS Security
- AI in Cyber Security leverages the industrial cyber security power of machine learning and data analysis to augment traditional security measures.
- Zero Trust Architecture brings a new security level in OT/ICS environment.
- How can the Industrial Metaverse help to secure our Industry 4.0 ?

David Prada - Cybersecurity IT/OT researcher at Howest

Laurens Singier - Cybersecurity IT/OT researcher, Ethical hacker at Howest

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.
11:00 AM – 11:15 AM
COFFEE BREAK
11:15 AM – 12:30 PM
- Auditorium
Industrial Environment Scanning and Enumeration
- AI in Cyber Security leverages the industrial cyber security power of machine learning and data analysis to augment traditional security measures.
- Zero Trust Architecture brings a new security level in OT/ICS environment.
- How can the Industrial Metaverse help to secure our Industry 4.0 ?

David Prada - Cybersecurity IT/OT researcher at Howest

Laurens Singier - Cybersecurity IT/OT researcher, Ethical hacker at Howest

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.
12:30 PM – 02:30 PM
LUNCH TIME
2:30 PM – 3:30 PM
- Auditorium
Exploitation in an Industrial Environment
Training
- Introduction to Industrial Control Systems
- Basics of PLC Programming
- Industrial Communication
- Scanning ICS networks
- Industrial Network & System enumeration
- Reversing proprietary industrial protocols
- Exploiting industrial control systems
Workshop
Hands on: Industrial CTF on the Fictile Factory
Fictile is a fast-growing fiction tile-producing company. Under the steady and continuous leadership of J.C, they are the unrivaled market leader in their sector since 2016. Their factory contains three halls. A hall with hydraulic presses, baking installation and a painting hall. To remain brand independent, the lead engineer of the factory decided to equip each hall with different types of industrial controllers. The three market leaders were chosen: Siemens, Beckhoff, and Phoenix Contact. According to investor K.C., there is no room in the budget for cyber-security. “Production must come first.”
Can you prove them wrong, by capturing all the flags?
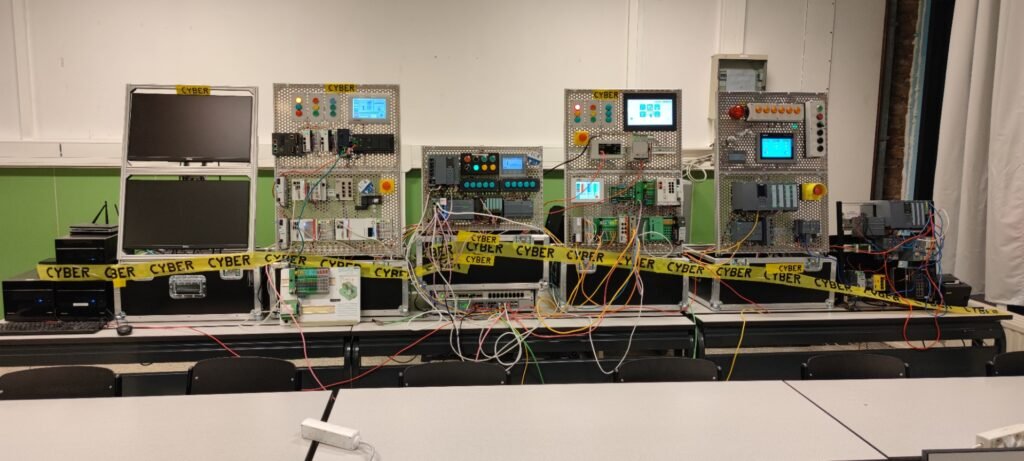

David Prada - Cybersecurity IT/OT researcher at Howest

Laurens Singier - Cybersecurity IT/OT researcher, Ethical hacker at Howest

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.
3:30 PM – 3:45 PM
COFFEE BREAK
3:45 PM – 5:30 PM
- Auditorium
Exploitation in an Industrial Environment
Lab work: Hands on – Industrial CTF on the Fictile Factory

David Prada - Cybersecurity IT/OT researcher at Howest

Laurens Singier - Cybersecurity IT/OT researcher, Ethical hacker at Howest

Kurt Callewaert - Howest Valorisation Manager Digital Transformation, Former Head of Research Applied Computer Science.
Sold out
05:30 PM – 06:30 PM
- Hub
Aperitif
06:30 PM – 10:00 PM
- Voyager Café
Gala Dinner at the Euro Space Center
Protection of mobile devices Day

Jeroen Beckers, mobile solution lead at NVISO, will do us the honor of teaching a whole-day class, divided in 4 talks, 3 sessions of exercices, a workshop, and a Q&A session.
8:30 AM – 9:00 AM
REGISTRATIONS
9:00 AM – 9:45 AM
- Auditorium
Intelligence: balancing the human and the digital
The digital solution can contribute to the security and safety of our communications, our writings and our productions, but we must never forget the human element, its share of responsibility and its possible shortcomings. Let’s talk about it together…
French presentation

Pascal PETRY - Deputy General Administrator of State Security (Belgium).
09:45 AM – 10:45 AM
- Auditorium
Introduction to Mobile Day + [Talk] Attack surface of mobile devices / application
Introduction to the principles for attacking mobile devices, specifically Android and iOs. Introduction to reverse engineering principles, which will be applied in the subsequent exercise.
10:45 AM – 11:00 AM
COFFEE BREAK
11:00 AM – 12:00 AM
- Freedom & ISS
[Exercises] Mobile Apps reverse engineering, CTF style (Part 1)
Cyber security challenges of the CTF type, focused on mobile security. To be solved in groups or on your own over 1h30. Progressive level of difficulty, from easy to difficult. Will conclude with a review of the challenges and their resolution.
NVISO Coaches
11:30 AM – 12:00 AM
- Freedom & ISS
[Exercises] Solution of the reverse engineering exercises
10:45 AM – 11:00 AM
COFFEE BREAK
12:00 PM – 01:00 PM
LUNCH TIME
01:00PM – 02:30PM
- Auditorium
[Talk] A review of current mobile malware trends
Review of techniques used by Android mobile malware, as Android is the primary target for mobile
01:00 PM – 02:00 PM
- Freedom & ISS
[Exercises] Mobile Apps reverse engineering, CTF style (Part 1)
Cyber security challenges of the CTF type, focused on mobile security. To be solved in groups or on your own over 1h30. Progressive level of difficulty, from easy to difficult. Will conclude with a review of the challenges and their resolution.
02:00 PM – 02:30 PM
- Auditorium
[Talk] Solution of the reverse engineering exercises
Review of techniques used by Android mobile malware, as Android is the primary target for mobile
02:30 PM – 03:30 PM
- Auditorium
[Talk] Introduction to tampering with Android apps
Review of some the techniques used to reverse engineer (Android) apps. Over one hour, the talk will focus on some of most prominent techniques.
02:00 PM – 03:00 PM
- Freedom & ISS
[Workshop] Mobile malware analysis
In the same spirit as the CTF in the morning, an Android app is provided for analysis in order for participants to identify, analyse and understand malicious components of the app.
03:30 PM – 05:00 PM
- Freedom & ISS
[Exercises] Modify Android applications to disable security features or add keyloggers. Note: we will announce the break during the session, which people will be free to join
Sandbox-based analysis guided by the NVISO team.
NVISO Coaches
04:15 PM – 04:45 PM
COFFEE BREAK
05:00 PM – 05:30 PM
- Auditorium
[Talk] Closing thoughts: mobile security in the coming 10 years
We will among others discuss:
- Privacy in mobile: key challenges, and the difference in philosophies of Google & Apple.
- The challengers to Apple & Google’s mobile OS domination, from geopolitical motives to privacy concerns.
- What lessons have OS designers drawn from advanced nation state attacks.
05:30 PM – 06:00 PM
- Auditorium
Q&A
3:30 PM – 3:45 PM
COFFEE BREAK
Our Program for the 5 days
The programme includes theoretical & practical courses
A break is scheduled every day in the morning and afternoon
The next editions of Cyberwal in Galaxia Program are already planned for 2024.
Gala dinner
Meat meal
Shrimp tartlet with avocado, grapefruit, and yuzu emulsion
Wine: Bourgogne cave de Viré « Macon Village » White
***
Prairie pork square from Majerottes, sautéed and schredded butternut squash, and chestnut parmentier
Wine: Château Tour Lescours Saint Emilion Red
***
Crunchy chocolate with mascarpone, coffee, and speculoos
Fish meal
Scallop osso bucco, herb parmentier, lobster béarnaise, snow pea freshness
Wine: Bourgogne cave de Viré « Macon Village » White
***
Roasted monkfish fillet, stewed leek, shellfish risotto
Wine: Château Tour Lescours Saint Emilion Red
***
Crunchy chocolate with mascarpone, coffee, and speculoos
Vegan meal
Sun-dried tomato and grilled bell pepper tartlet, sesame-grilled tofu with sweet and sour vinaigrette, and snow pea freshness
Wine: Bourgogne cave de Viré « Macon Village » White
***
Sautéed mini broccoli with soy, edamame beans, pesto, and sweet onion fritters
Wine: Château Tour Lescours Saint Emilion Red
***
Fruit tartare and lime sorbet
Registration
Register now to be a part of this exclusive event!
End of registrations on 27/11 at 12 PM
*Your registration includes:
- Courses & practical work
- Shuttle bus from Mercure hotel to Galaxia
- Meals (lunch & coffee breaks)
- VIP visit to Euro Space Center
- Gala dinner
Not included:
- Hotel
- Breakfast
- Evening meals
Previous edition
2022 Cyberwal in Galaxia Program
12 – 16 December 2022
Register now!
2023 Cyberwal in Galaxia . .. ...
OUR BEST PARTNERS
This Program, which is financed by the Walloon Region, is organized by IDELUX Development (the Economic Development Agency of Belgian Luxembourg) and under the authority of the scientific committee chaired by Mr Axel Legay, Professor of cybersecurity at the UC Louvain.








With the support of